Fortifying Security for Multi-WAN Network
Connectivity and security are the top concerns for every organisation. The security threat is growing as enterprises are deploying more apps in the cloud and expanding more branch offices. Q-Balancer delivers advanced security as a layer of protection to branch networks, while protecting business continuity against WAN outages. Through properly configuring its inbuilt security mechanisms, it can be a primary firewall, or simply works nicely with the security solution that is already in place.
> Stateful Inspection Firewall
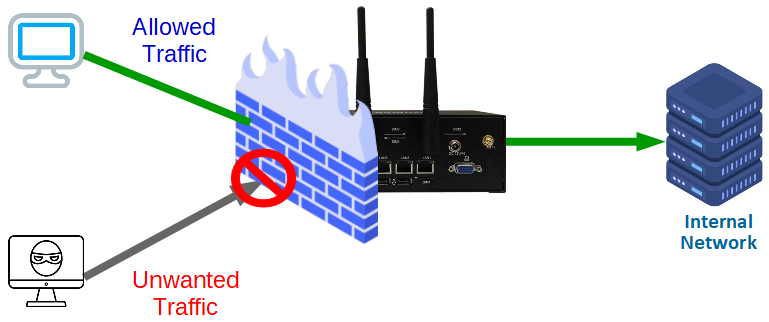
Stateful Inspection Firewall
Q-Balancer solution is incorporated with stateful inspection firewall that allows or blocks traffic based on state, IP, port, and protocol. The inbuilt firewall monitors all activity from the opening of a connection until it is closed. When new packets arrive, the inbuilt firewall compares information in the packet header to the state table and determines whether it is part of an established connection. If it is part of an existing connection, then the packet is allowed to pass through without further analysis. If the packet doesn't match an existing connection, it is then evaluated according to the rule sets for new connections.
Top Benefits
> Fortified network security
> Application, user and device control
> Enhanced compliance
> Enterprise-grade encryption
> Improved productivity
> Visibility
























































